Introducing Atomicwork’s Agentic IGA

Access provisioning today is reactive, manual, and brittle. On paper, it is simple - the right people get the right access at the right time, for the right duration. In reality though, it rarely works that way.
Every quarter, IT teams end up in the same loop, fielding continuous access requests from employees, and going through spreadsheets and access lists to answer a deceptively simple question: who has access to what? They hunt for the obvious red flags like blanket admin permissions or long-forgotten privileges, and revoke what looks dangerous or outdated.
After all, nobody should be over-privileged when it comes to access.
Where traditional IGA falls short
To bring order to the chaos, organizations turned to software for Identity Governance that promised visibility and ease-of-use. But for many teams, managing identity and access has become the most complex initiative they have to run. Review cycles are often just performative exercises. Compliance means managing the system rather than actually reducing risk.
The root problem is not lack of effort, it is structural.
- Requests from employees come in free form and through any and every channel.
- Access approvals are slow and context-poor.
- Provisioning automations don’t consider employee context and require extensive setup and maintenance.
- Deprovisioning is not automated, so it’s often missed when roles change or projects come to an end.
- Governance ends up being a quarterly cleanup exercise instead of the continuous process it should be.
The promise of Agentic IGA
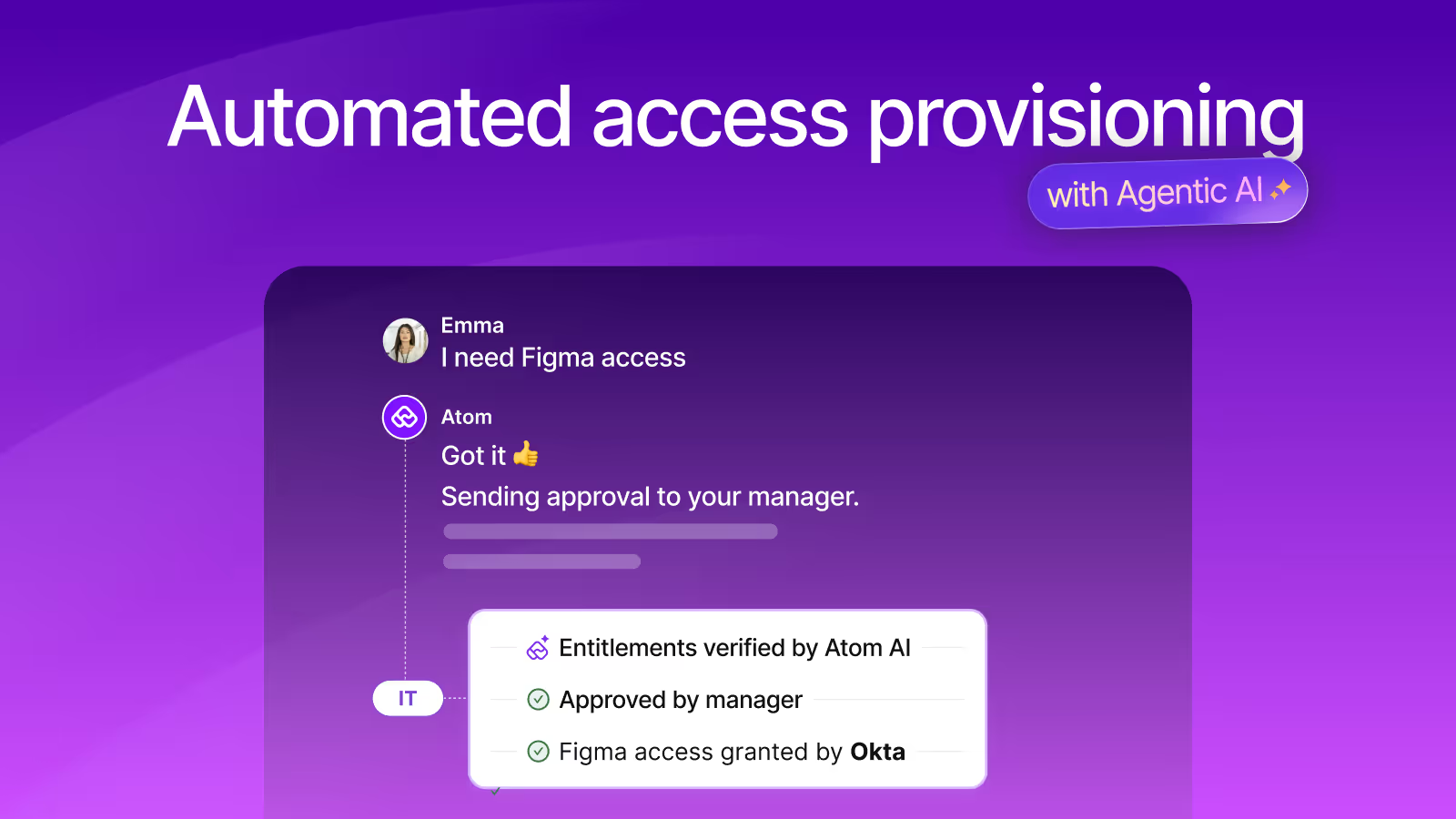
Today, we’re launching Agentic IGA to change this fundamentally by making access provisioning and deprovisioning autonomous.
- Employees ask for access in the flow of work through 5+ channels including browser, MS Teams and Slack instead of having to navigate to a portal and fill out a form that doesn’t cover their need or answer their questions.
- Atom, the Universal AI Agent, conversationally requests for information, contextualizes asks for employees and uses policies and entitlements to intelligently provision access.
- By connecting their IdP systems to Atomicwork, IT teams enable level 2 automation of access requests in an autonomous manner that offloads work from service teams and enhances the employee experience.
This agentic access management automation is made possible through a specialized IGA agent, that autonomously handles all access requests.
At Atomicwork, we launched our IGA agent to change this fundamentally by moving access provisioning and deprovisioning to be autonomous. The agent understands intent, role, and risk in real time, automates provisioning and de-provisioning across systems, and keeps access in sync as people and responsibilities change. Instead of chasing access after the fact, IT teams can make least-privilege the default.
Why solve for access governance now
Building Agentic IGA forced us to step back and question some assumptions about how identity governance and administration should work and what customers are looking for.
What we learned quickly is that the problem isn’t just tooling, it’s a combination of technology choices and broken processes that have quietly become accepted as “how things work.” Fixing access governance requires unlearning a few defaults, both in how systems are designed and how teams operate. Here’s what stood out for us:
1. Access delays are productivity killers, not just IT friction. When access isn’t immediate, work simply stops. We saw cases where employees waited days for read access to a single dashboard just to finish an analysis. Systems that slow access in the name of safety end up costing the business far more in lost time than the risk it’s trying to prevent.
2. Intent matters more than rules. A request like “need access to Salesforce” is meaningless without context. Is it read-only for a one-week analysis? Admin access for an ongoing role? Systems that don’t provision based on intent default to broader permissions which then become audit risks later. Atomicwork’s IGA agent is tailored to deeply reason over the business justification and intent to provide just the right access.
3. Integrations are the backbone. Early on, we invested in tighter integrations with IdP and HRIS systems so the agent could understand context. Context of users, groups, policies, hierarchies and approvers. This context reduces the need for IT to rebuild access logic twice - once in the IdP and once in Atomicwork.
4. Deprovisioning fails because it is reactive and loosely owned. Access rarely gets removed when roles change or projects end. Instead, it shows up months later during an audit or review cycle. We learned that unless deprovisioning is automatic and tied to real signals (role change, project completion, inactivity), it will always be missed. Provisioning and deprovisioning has to deeply tie up with users’ lifecycles.
5. Finally, making the IGA work required rethinking the underlying architecture. To deliver instant, context-aware access, we couldn’t rely on a single rules engine or one-size-fits-all model. We had to invest in a fast, accurate multi-agent system, one that uses the right models for intent detection, risk evaluation, and policy enforcement, so decisions could be made reliably in real time.
If there’s one takeaway from building Agentic IGA, it is that access governance shouldn’t be a quarterly cleanup project. It should be a living system that moves fast without accumulating risk and debt in the background.
That's what we set out to solve. Autonomous provisioning that understands intent, enforces least-privilege by default, and keeps access in sync as your organization evolves.
If you'd like to see how it works, sign up for a quick walkthrough here.
Frequently asked questions

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph
You may also like...