How to automate access provisioning (and save 2,500+ IT team hours/year)
Your engineering team needs GitHub access. Your sales team needs Salesforce. Your design team needs Figma. And your IT team? They're drowning in access requests, following up with approvers and manually clicking through admin panels to add users.
The average knowledge worker juggles 11 different applications daily just to get their job done, with some using over 26 apps according to Gartner research. Access provisioning thus becomes one of those essential yet repetitive tasks that burn your employees’ and IT team's time.
Let’s pause for a moment here. When time means money in business, we decided to dig deeper and put a number (a very conservative estimate) to the wasted time and money.
Why automate access provisioning?
To estimate the time taken for the provisioning process, let’s break down what manual provisioning looks like in practice:
- With manual provisioning, employees usually don't know what access they need or who to ask
- They reach out to the IT team, who then sends them to a portal to submit a ticket
- They then wait for the manager/app owner approval
- Then IT either grants access (if they have admin rights) or pass the request to yet another team
For an organization with 5,000 employees, let’s assume each employee raises roughly two access requests a year. If each request takes 15 minutes to be manually serviced, that's 2,500 hours your IT team could've spent on strategic work instead of repetitive tasks.
If the median IT staff pay is $22 per hour, then that's a total of $55,000 wasted annually on tasks that could be automated. And that doesn't include the cost of your employees being stranded without the tools they need—10,000 times a year.
Manual provisioning doesn't just drain your team’s waste time; it also:
- Increases security risks due to delayed deprovisioning
- Drives up unnecessary license costs
- Requires significant configuration across disconnected tools
- Forces security teams to spend hours on manual audits
To free your IT team time and reduce the long wait times spent by your employees, you can automate the entire provisioning workflow with agentic AI. Let’s see how.
How automated access provisioning works?
Organizations typically use identity and access management platforms like Okta or Microsoft Entra to handle identity governance, policy enforcement, and track compliance.
However, native IAM platforms do not support on-demand access requests for employees on channels they already use, introducing friction in the provisioning process from an end-user perspective. Moreover, handling approvals and follow-up notifications can’t be done inherently within these tools.
Integrating your IAM tool with a modern ITSM platform can help address these challenges by allowing employees to submit access requests via collaboration platforms like Slack or MS teams.
You can also automate approvals and notifications through the service management platform for one seamless provisioning workflow.
Here’s what an example of what an end-to-end automated provisioning workflow looks like.
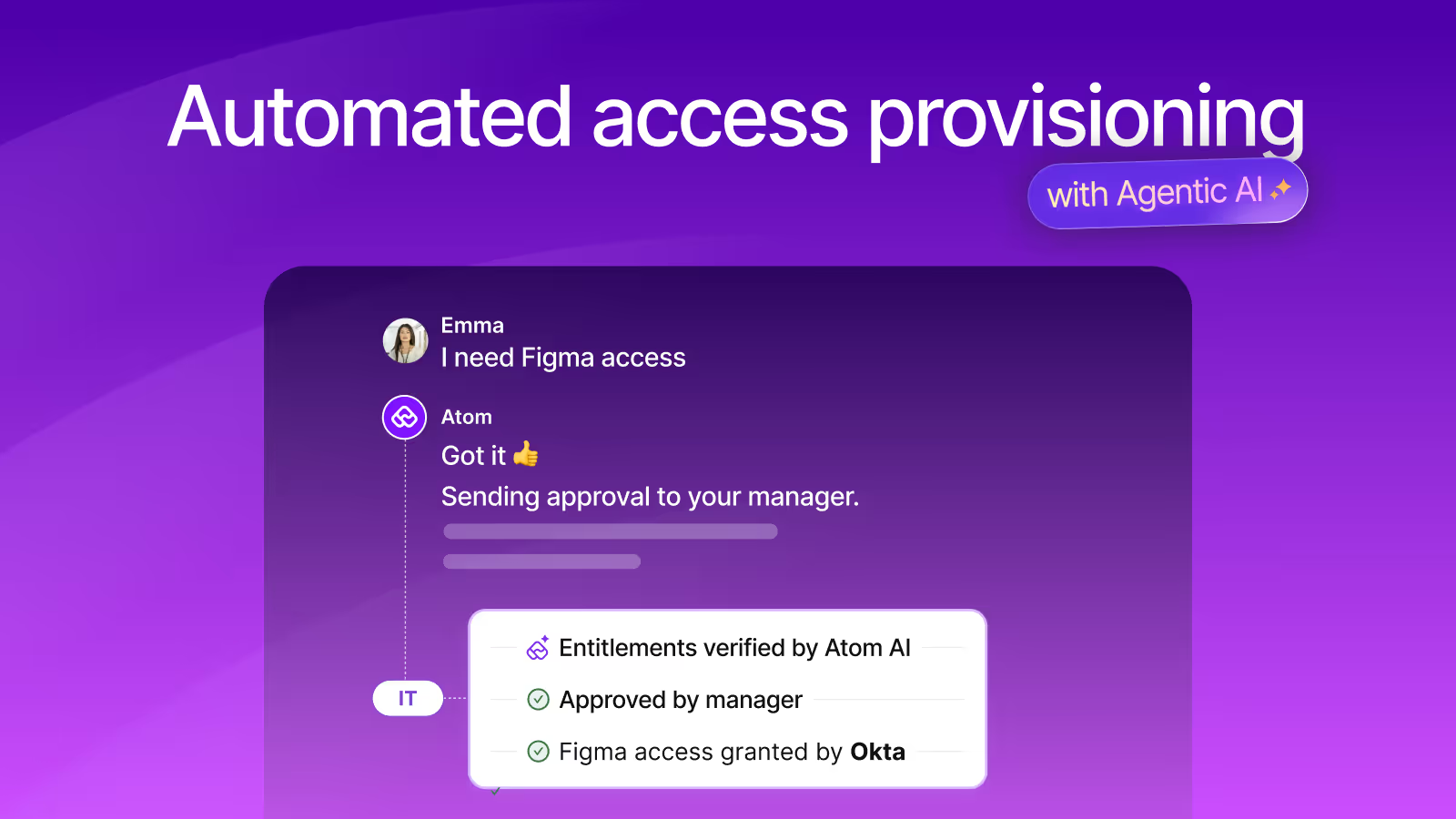
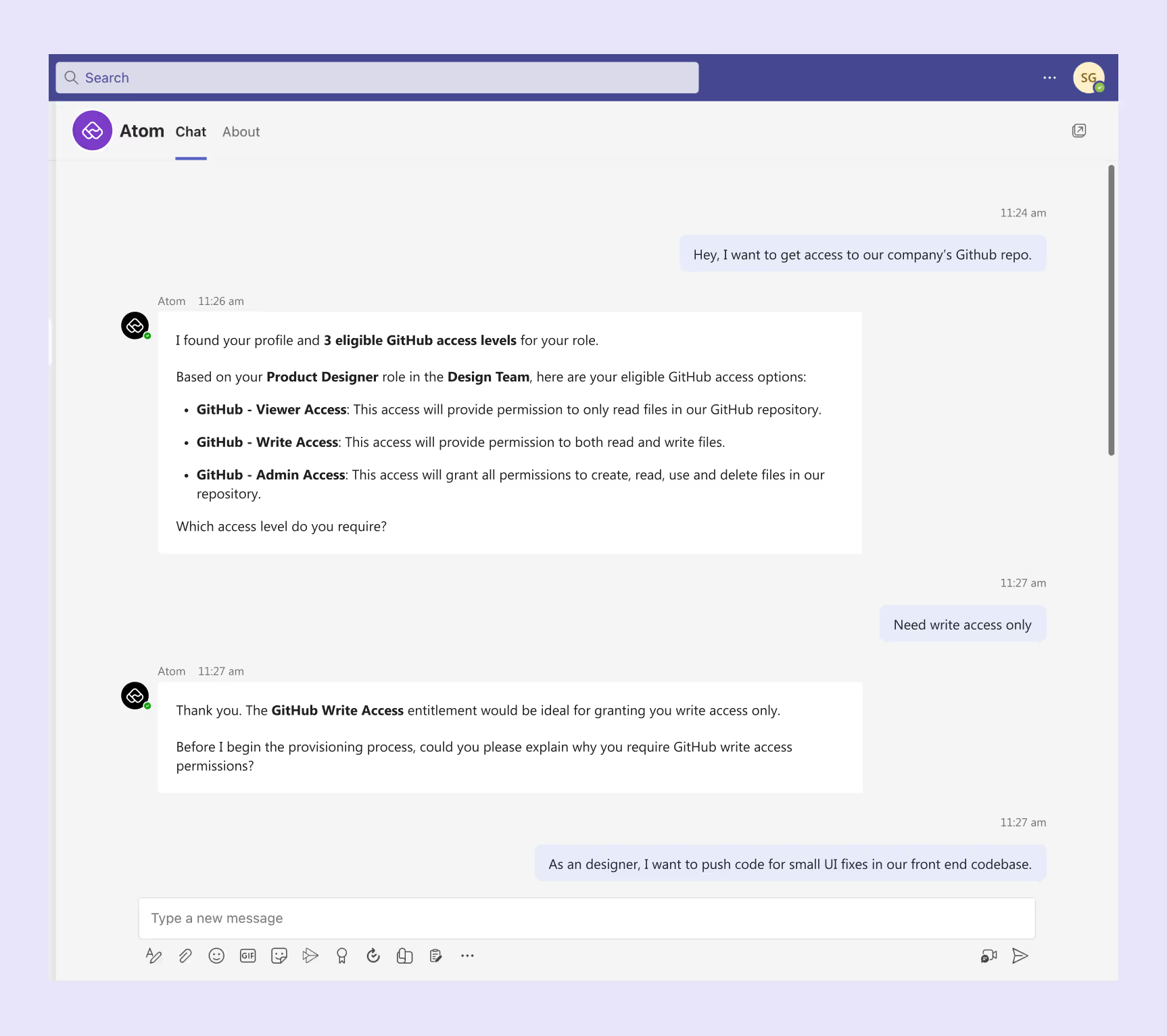
Let's say someone from your engineering team needs access to GitHub. The employee can just ask your AI assistant on Slack, Microsoft Teams, or in their browser for what they need, in plain language—Can I get access to the Github design repo?"
The AI assistant understands the request, checks which entitlements they're eligible for based on your policies, and handles the entire provisioning process autonomously.
Employees can even ask discovery questions like "What role can I get for the design GitHub repo?" or "What's my current access in Github?" The agent provides instant answers and transparency into their access rights.
If approval is needed, the request automatically routes to the right manager or app owner. If it's completely self-serve, access is granted immediately without having to fill forms or open portals.
Here’s how you can get started.
1. Connect your identity providers
Start by integrating Okta or Microsoft Entra with your service management platform like Atomicwork. All applications instantly sync into a centralized app catalog that automatically pulls in entitlements, policy, owner, and user information from the identity provider. For non-SCIM apps, you can also add them directly to the service management software.
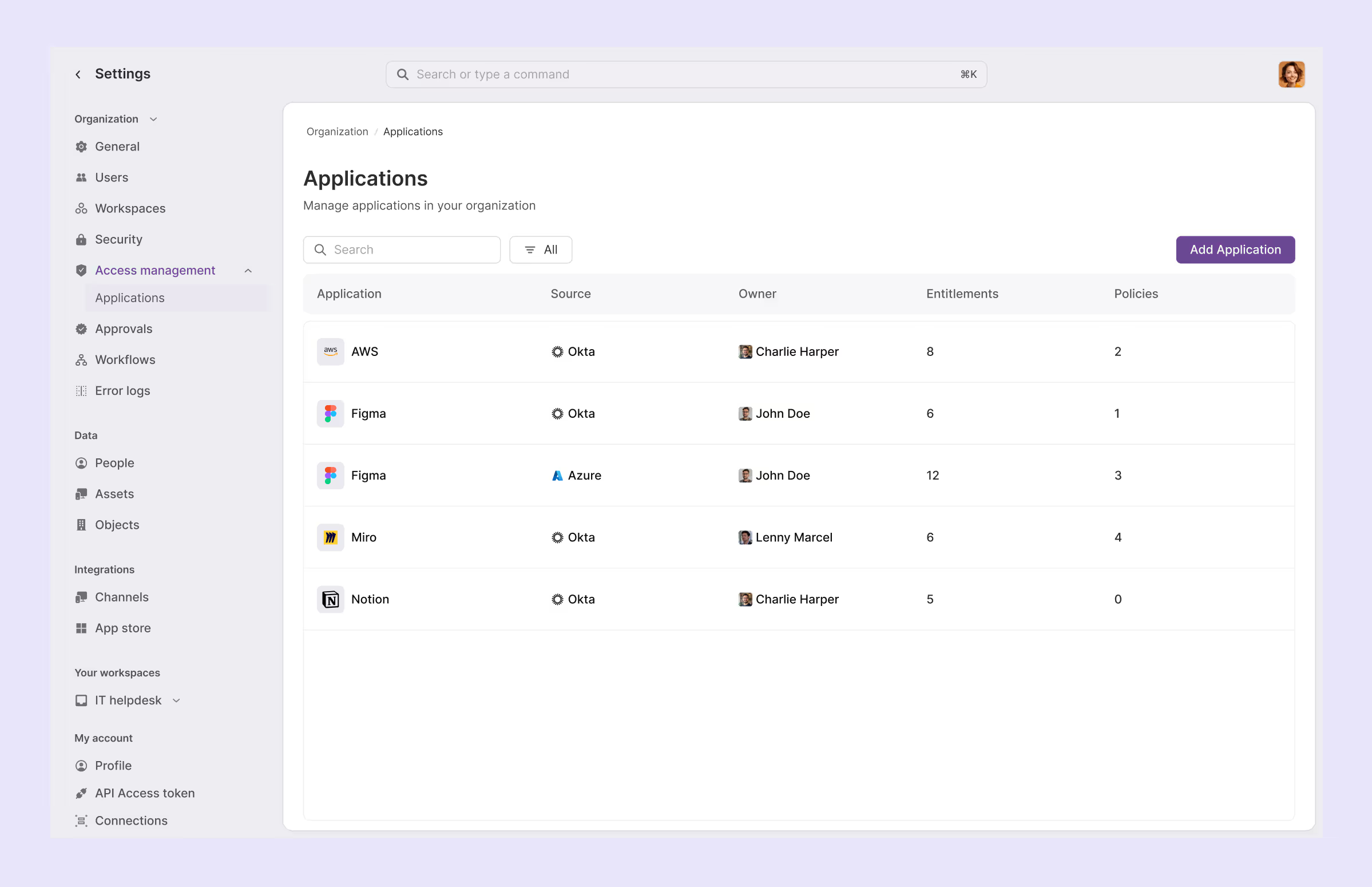
2. Configure user entitlements
Once the apps are synced, you can view every app from the connected IdP on a single dashboard.
You can nominate app owners, configure entitlements for each application, and define flexible approval policies all a single place.
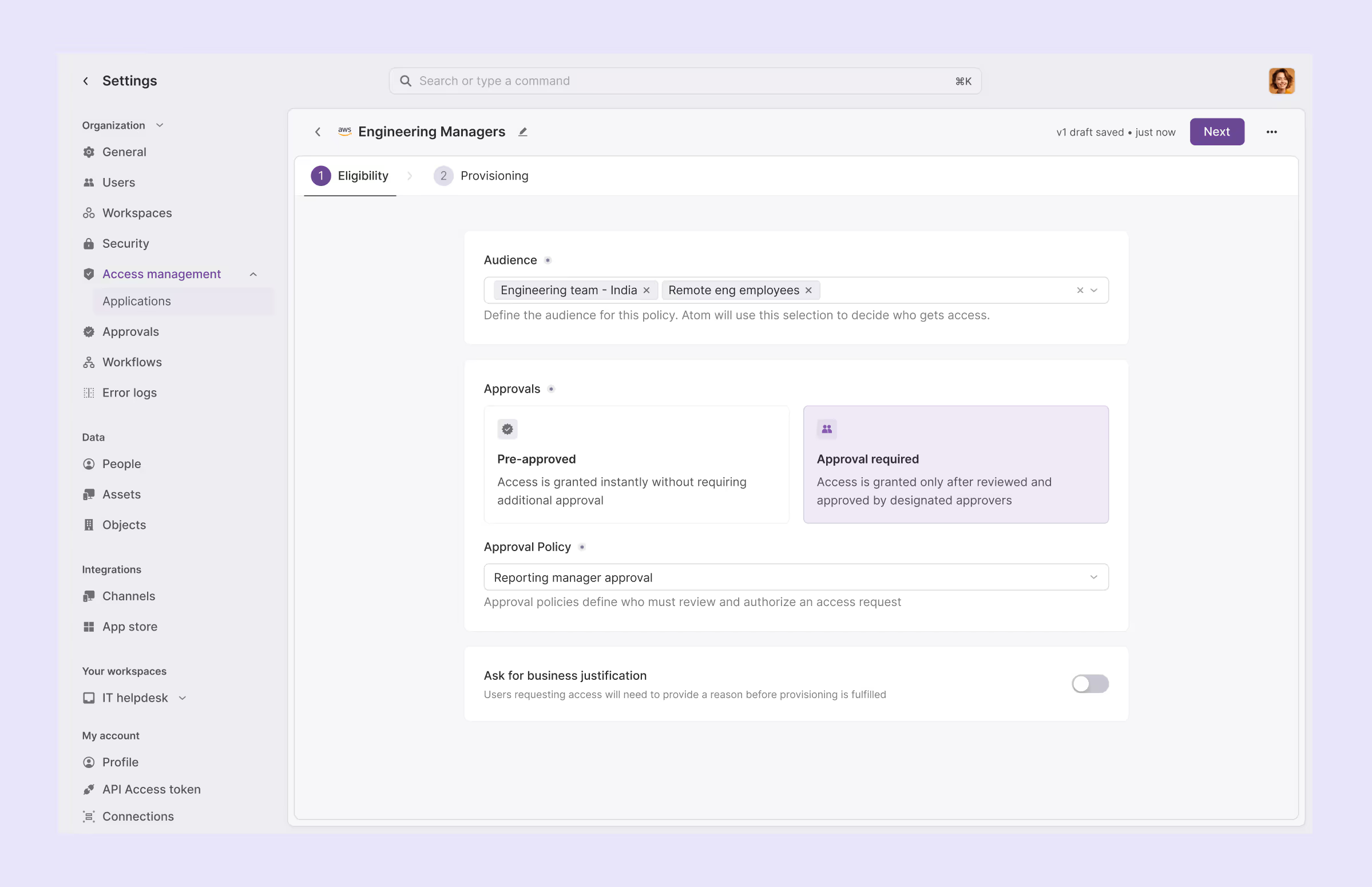
3. Design approval workflows with intelligent fallbacks
Map out approval requirements based on application sensitivity and user roles. Build out your workflows that adapt when things don't go according to plan.
- Configure primary and backup approvers for different request types
- Set automatic escalation when approvers don't respond within defined timeframes
- Handle role changes by automatically removing outdated permissions while adding new ones. You can also use flexible placeholders like "App Owner" within your approval policies so that they adapt automatically as the app ownership changes.
- Create exception handling for urgent requests that need immediate access
While setting up approval policies, you can have global approval policies that apply across all apps or define granular access policies specifying which user segments can access which specific entitlements.
For instance, when someone from your sales team requests for CRM edit access, you’ll want to have it approved by the Sales VP to protect sensitive client details.
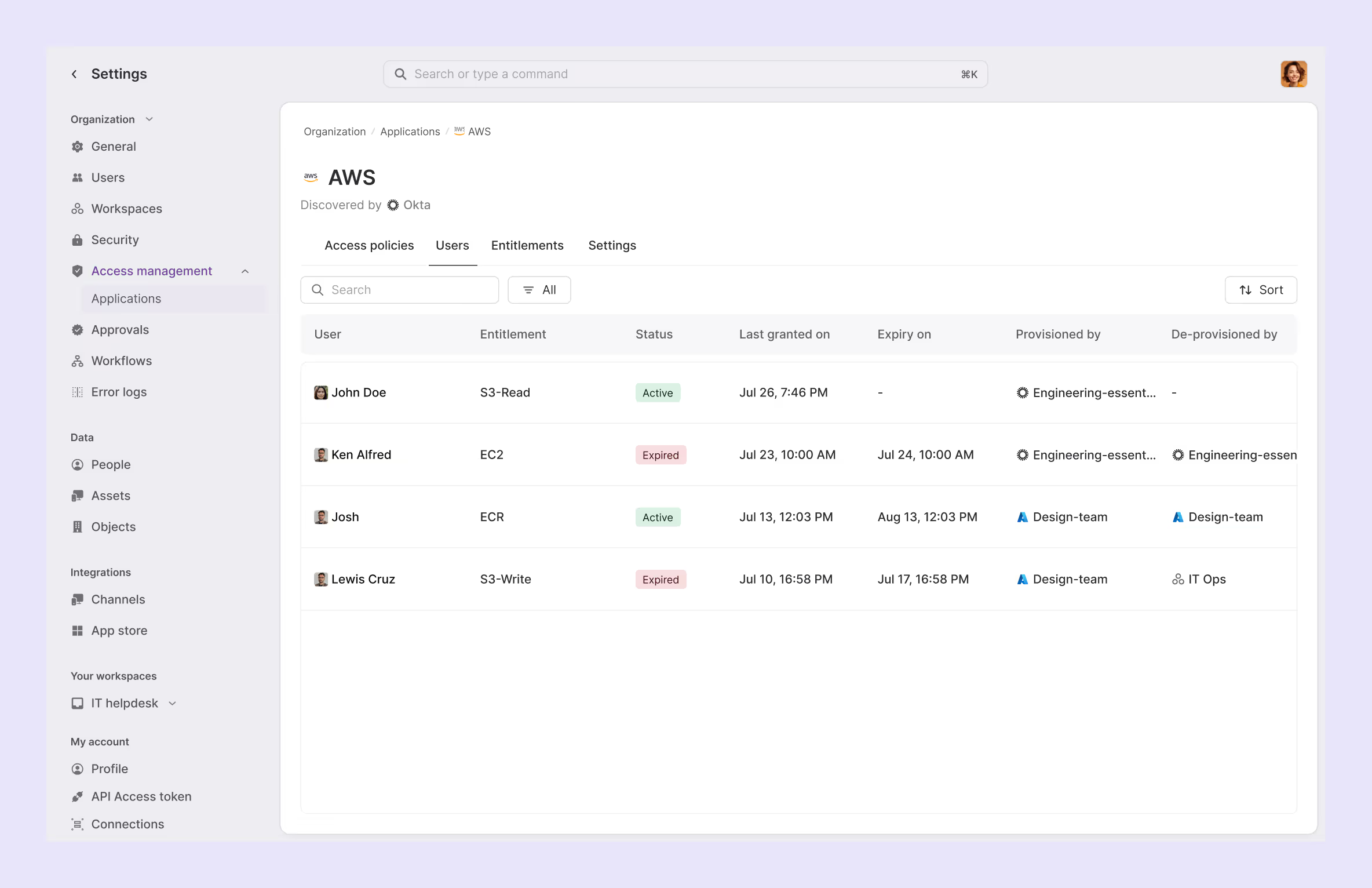
4. Establish built-in governance and compliance records
Set up the logging on your service management platform to track all provisioning activities, approval decisions, and system changes. Every workflow should align with your security policies and maintain visibility into user activity for monitoring and issue detection.
- Track access grants in one view: See all access grants tied to each entitlement in one place without digging through multiple systems.
- Maintain comprehensive audit logs: Track every change to app users, entitlements, and policies for complete compliance visibility.
- Empower application owners: Give app owners or admins their own focused view where they can edit entitlements they own and see all grants against their applications.
5. Enable conversational access requests
Configure chat-based request channels in Slack and Microsoft Teams so employees can request access using natural language instead of navigating forms and portals.
Your AI assistant on these channels should be able to understand requests like "I need Salesforce access for the new client project" and translate them into proper provisioning workflows.
Set it up to gather missing information through follow-up questions and provide status updates throughout the approval process.
For example, if an employee wants to create customer surveys and is unsure of the tool to use, they should be able to ask the intelligent assistant the tool they’d need and access to that particular tool that matches their requirements.
The bottom line
Automated access provisioning saves your IT team time and money while eliminating all the grunt work needed to coordinate with stakeholders across different apps, with minimal implementation effort.
IT teams can also accelerate their onboarding processes, improve security through automated deprovisioning, and strengthen compliance processes that happen automatically rather than through manual oversight.
Ready to see how Agentic AI-powered access provisioning can turn those 2,500 wasted hours into strategic advantage? Talk to our team now.
You may also like...

































