


.avif)

Learn our approach to building reliable and secure enterprise AI and modern service management platform.
Visit our Trust Center
We are committed to upholding best-in class standards in customer security, data processing, privacy, and compliance.

We meet globally recognized security standards and prove it with independent audits.

Your data is yours. Always. You control the data that gets indexed, modified, or deleted.

Using AI and LLMs introduces unique data handling considerations which we strive to meet.

Our infra is hardened through layered defenses and security is embedded in every phase of development.
We prioritize your business safety, adhering to top enterprise security, compliance and privacy standards.
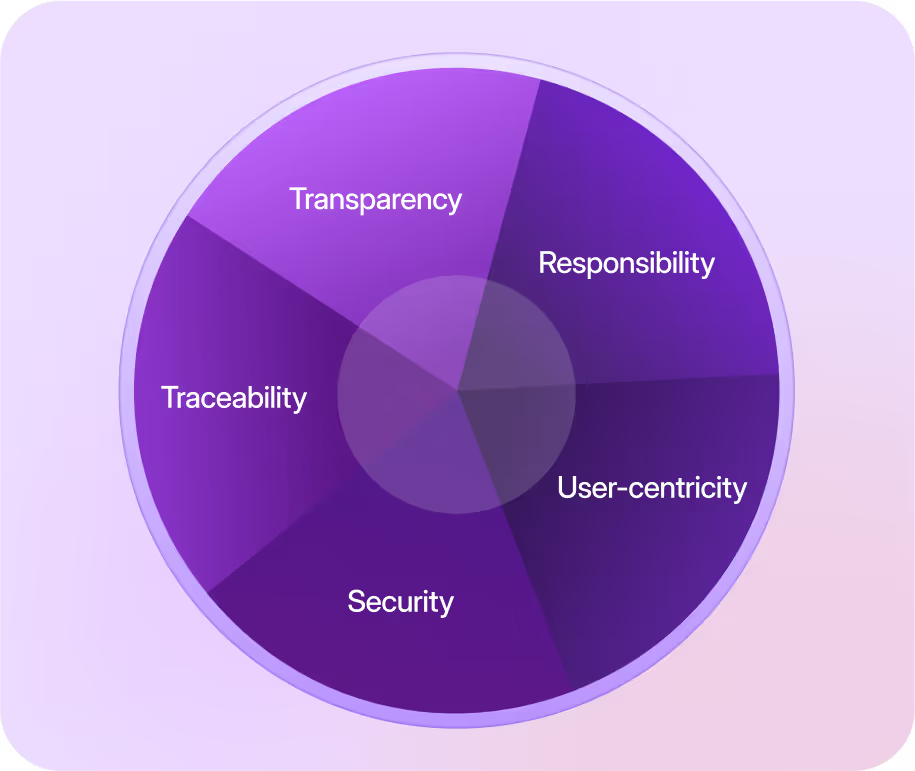
Atomicwork has been designed to protect your data at every step along the way.
Atomicwork's ensemble AI model architecture is self-hosted on a secure cloud platform and designed to leverage the advantages of different models for different service management and employee experience usecases.
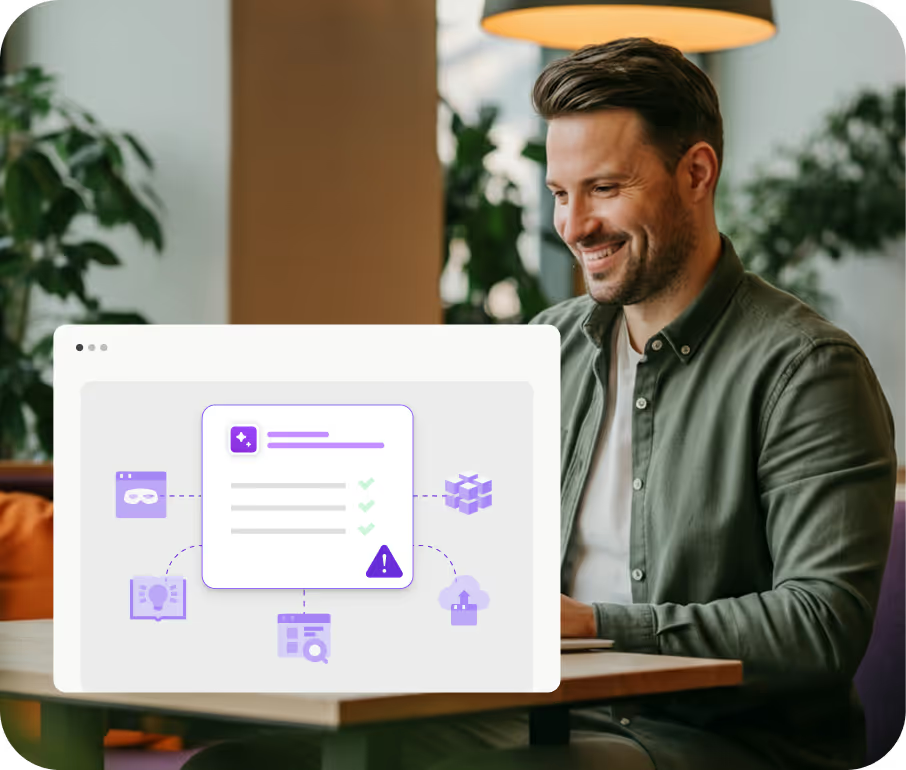
Atomicwork has built layers of security measures to make sure user data is safe, secure and properly used. We also use extensive testing techniques to ensure AI models perform reliably under various conditions.
Atomicwork has been designed, ground-up, to ensure that maintaining data security and user privacy is paramount.

Simplify access and enhance security by leveraging your enterprise IAM platform's SSO capabilities.

Atomicwork inherits permissions from source docs and systems, and allows teams to configure content ACLs.

Content syncs with source applications, maintaining compliance and consistency, reducing risk of outdated information.

Atomicwork provides contextualized answers based on a user's context (location, department etc.)

Atomicwork shows the math when generating answers or providing insights by linking to source information.

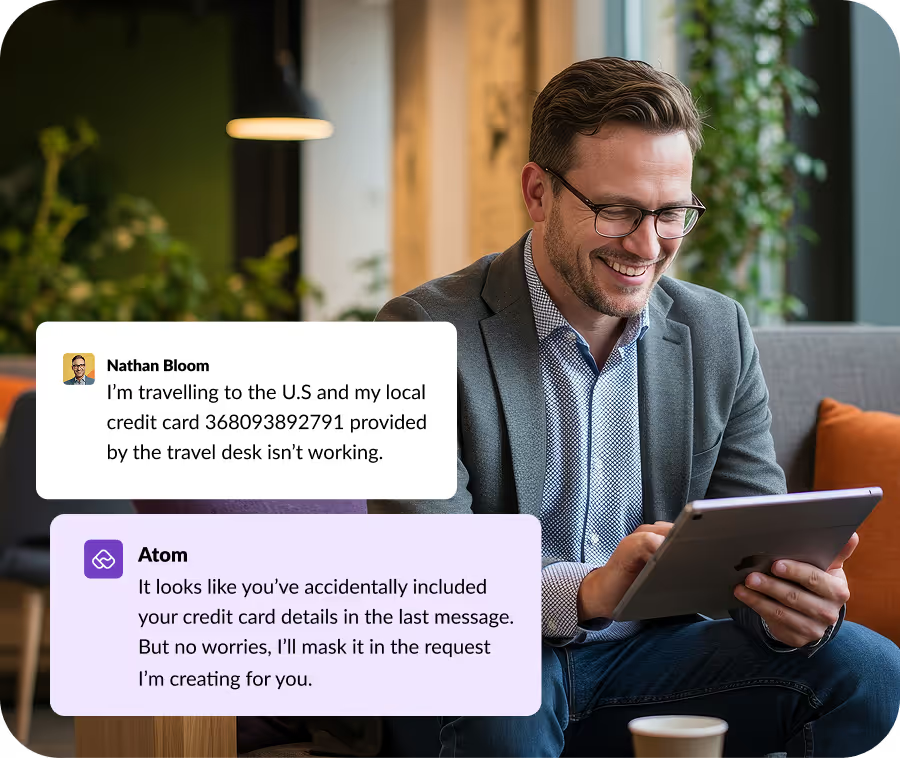
Atomicwork maintains user privacy by redacting PII in all circumstances, including data ingestion.
Please use one of the options below to get in touch with our security team.
We are committed to working with researchers to verify, reproduce and respond to legitimate reported security vulnerabilities.
Learn how we identify and mitigate risks, implement best practices, and continuously develop ways to improve our security posture.
We give you control over your personal data. You can access your data, delete it, and manage how it gets used.
Are you interested in having a discussion with our security team? Send us an email with more information and we'll get back.

Yes, you can choose the region to store your data. Atomicwork offers data residency options in approved regions, hosted on secure cloud infrastructure. Your data is always encrypted end-to-end using AWS RDS encryption, role-based access control (RBAC), and data loss prevention (DLP) measures.

Our platform is designed for high service availability through robust infrastructure, redundancy, and failover mechanisms. We provide an SLA-backed uptime guarantee with regular testing that help us ensure continuous uptime and reliable performance for our users.

No, the Universal Agent does not integrate with other ITSM platforms. Atomicwork is a full-stack service management platform with built-in agentic workflows delivering a complete, enterprise-grade solution for all your service needs. Our systems follow 24/7 SIEM monitoring with automated alerts and security workflows. If a breach is observed, we follow the documented incident response protocols to quickly address any disruptions, notify affected customers promptly, and provide a post-incident report with remediation details.

Yes, it learns from sources like Confluence, Google Drive, SharePoint, Notion and Slack/Teams to provide accurate, organization-specific answers. It supports all document formats, including PDFs and spreadsheets for structured data retrieval. It also taps into system-of-record sources like Jira, Salesforce, and Intune to ensure responses reflect real-time organizational context.No. Customer data is not used to train AI models unless explicitly permitted.

Atomicwork connects with apps across the enterprise tech stack including Okta, Azure AD, Google Workspace, Jira, Salesforce, and more—enabling the Universal Agent to pull real-time data, execute workflows, and provide trusted answers. Yes. We hold SOC 2 Type I & II, ISO 27001, ISO 27017, ISO 27018, ISO 27701 certifications, and comply with GDPR, CCPA, HIPAA, and CSA STAR Level 1.

Atomicwork provides role-based access control, AI guardrails, and industry-standard compliances through the TRUST framework to ensure the Universal Agent's responses are compliant, permissions-aware, and free from unauthorized data exposure.We follow security best practices for API integrations, comply with CASA Tier 3 for Google Apps, and hold Microsoft 365 certification for secure deployment.

We isolate AI and LLM processing environments, encrypt all data in transit and at rest, and never use customer data to train public models. Access to AI systems is fully audited with strict input validation, adversarial testing, and continuous monitoring of AI interactions.
