An IT admin’s playbook to operationalizing compliance in change management

Your compliance audit is due next month. If your change management still runs on spreadsheets, email threads, and the memory of one long-tenured teammate, you’re setting yourself up for trouble. When auditors ask about segregation of duties or rollback procedures—you’ll face the same painful lesson thousands of IT teams have learned the hard way: compliance isn’t optional anymore.
Over the past year, what I’ve heard from countless IT leaders is clear: compliance doesn’t have to mean more bureaucracy. It’s about creating a change management process that both satisfies auditors, makes day-to-day operations more predictable, without extra overhead.
We present our learnings from helping enterprise IT teams be compliance-ready in their IT change management processes in this post. Let’s dive in.
1. Get smart with risk planning by classifying changes properly
While change classification simplifies your processes, it also serves to mitigate the associated risks. By classifying changes up front, you create the visibility needed to apply the right level of governance to each type. Low-risk changes move quickly, while high-risk changes get the scrutiny they deserve.
A few pointers to keep in mind while you build the processes for each change type include:
a. Standardize approval processes for different types of changes
- Set standard changes to be pre-approved, low-risk activities, such as adding users to existing groups or applying security patches from approved vendor lists. These can then flow through automated workflows with minimal human intervention.
- Regular changes require complete assessment and approval through your Change Advisory Board. This includes new application deployments, infrastructure modifications, and any change affecting multiple systems. These get complete impact analysis, testing requirements, and formal approval processes.
- Emergency changes bypass normal approval timelines when systems are down or security incidents demand immediate response. Emergency doesn't mean undocumented. These require post-implementation review and retroactive approval within 24-48 hours.

Pro tip:
IT admins can define workflows for every change per their IT environment, keep teams aligned, and cut down on repetitive setup for every new change.
Using customizable change templates, you can:
- Describe clear stages (e.g., Risk Analysis → Planning → Implementation → Review) so that every change follows a predictable path.
- Add fields that matter the most to you—like category, affected systems, or rollout type—so no critical detail gets missed.
- Build in tasks and approvals at each step, assigning them to the right stakeholders from the start.
- Control dependencies on each step in a sequence to prevent out-of-order actions, like blocking deployment until final approval.
- Automate with specific conditions for different actions based on form inputs or change type.
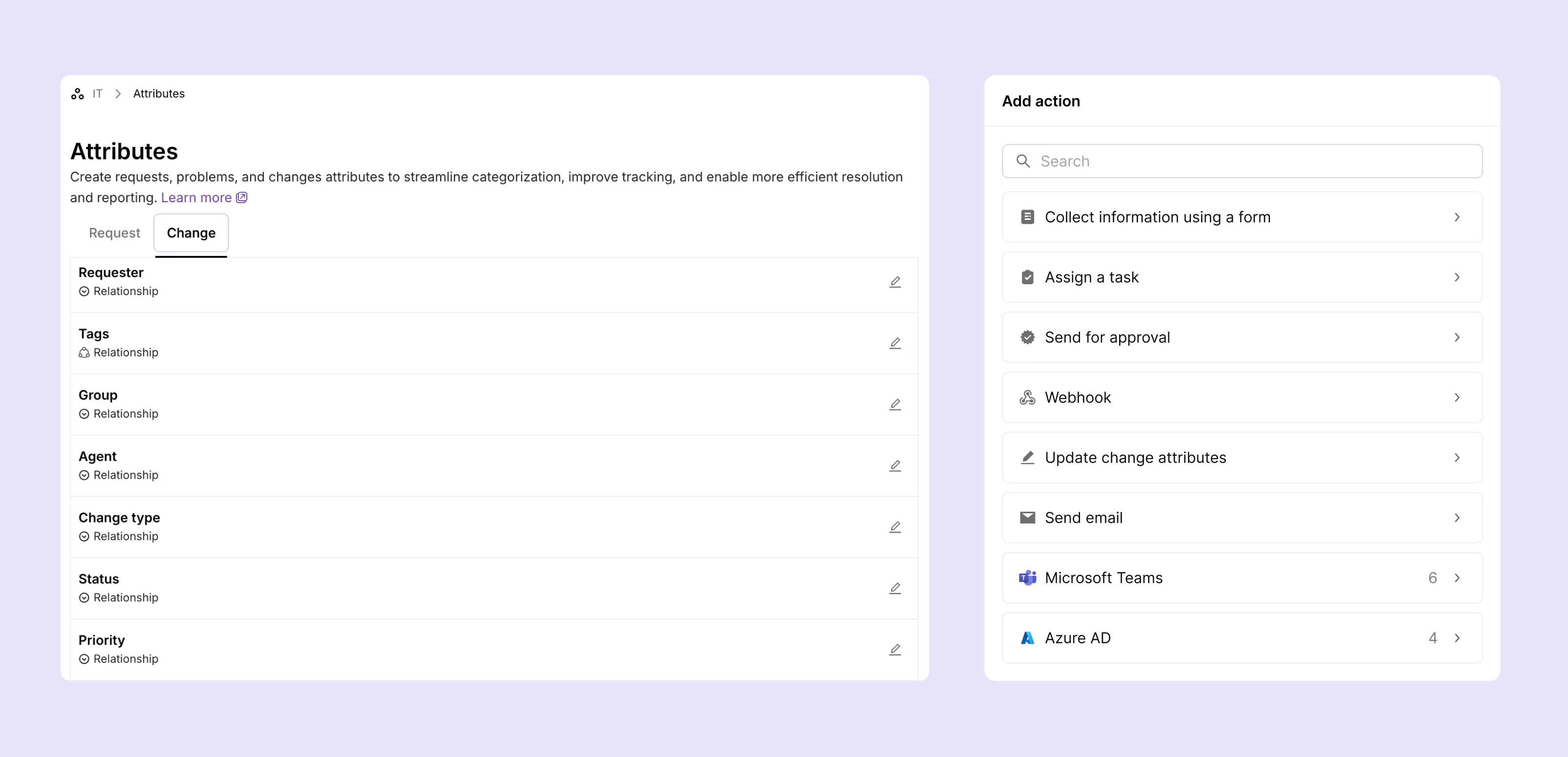
b. Implement formal scoring systems
- Impact assessment shouldn't be guesswork. Develop standardized criteria that consider technical complexity, affected users, business process disruption, and potential financial impact. A simple 1-5 scale works better than complex matrices nobody uses consistently.
- Urgency scoring evaluates timing requirements and business pressure. Not every "urgent" request needs emergency handling. You can use detailed risk assessment forms to get the necessary details and auto evaluate how critical the change is.
- Based on the technical complexity, number of affected users, process disruption, and potential financial impact you can then automatically calculate the risk score. The subsequent workflows can be triggered according to the score calculated, routing low-risk changes through fast approval cycles while high-risk changes trigger additional reviews and CAB oversight.
c. Build automatic escalation triggers
- Define clear thresholds that automatically escalate changes to senior management or specialized review boards. When changes exceed predetermined risk scores, cross multiple business domains, or involve critical infrastructure, they trigger additional oversight without manual intervention.
- Document these thresholds explicitly and make them visible to everyone submitting changes. This prevents surprises and helps teams understand why specific requests require additional approval steps. It creates audit trails showing high-risk changes received appropriate scrutiny.
2. Prioritize governance structures and access controls
When approval processes exist only in email threads and verbal conversations, you can't prove compliance even when you're following good practices. Most organizations treat governance as something that occurs after decisions are made, rather than as the framework that guides decision making.
a. Establish formal change advisory boards
- Your CAB is a decision-making body with defined membership, apparent authority, and documented processes. Include representatives from IT operations, security, business stakeholders, and compliance. Each member should have specific expertise and voting authority for different types of changes.
- Schedule regular CAB meetings with defined agendas and advance notice requirements. Ad-hoc decisions should be exceptions, not the norm. When emergency changes require immediate approval, document the decision-making process and validate it at the next scheduled meeting.
- Document every CAB meeting with attendees, decisions made, rationale for approvals or rejections, and action items in a centralized system.
b. Implement digital approval workflows
- Replace email approvals with workflow systems that capture digital signatures tied to user identities. When someone approves a change, the system should record their identity, timestamp, IP address, and any comments or conditions attached to the approval.
- Build approval workflows with SLA timers and automatic escalation. If approvers don't respond within the defined timeframes, requests should be escalated to backup approvers or management. This prevents changes from stalling while maintaining accountability for approval decisions.
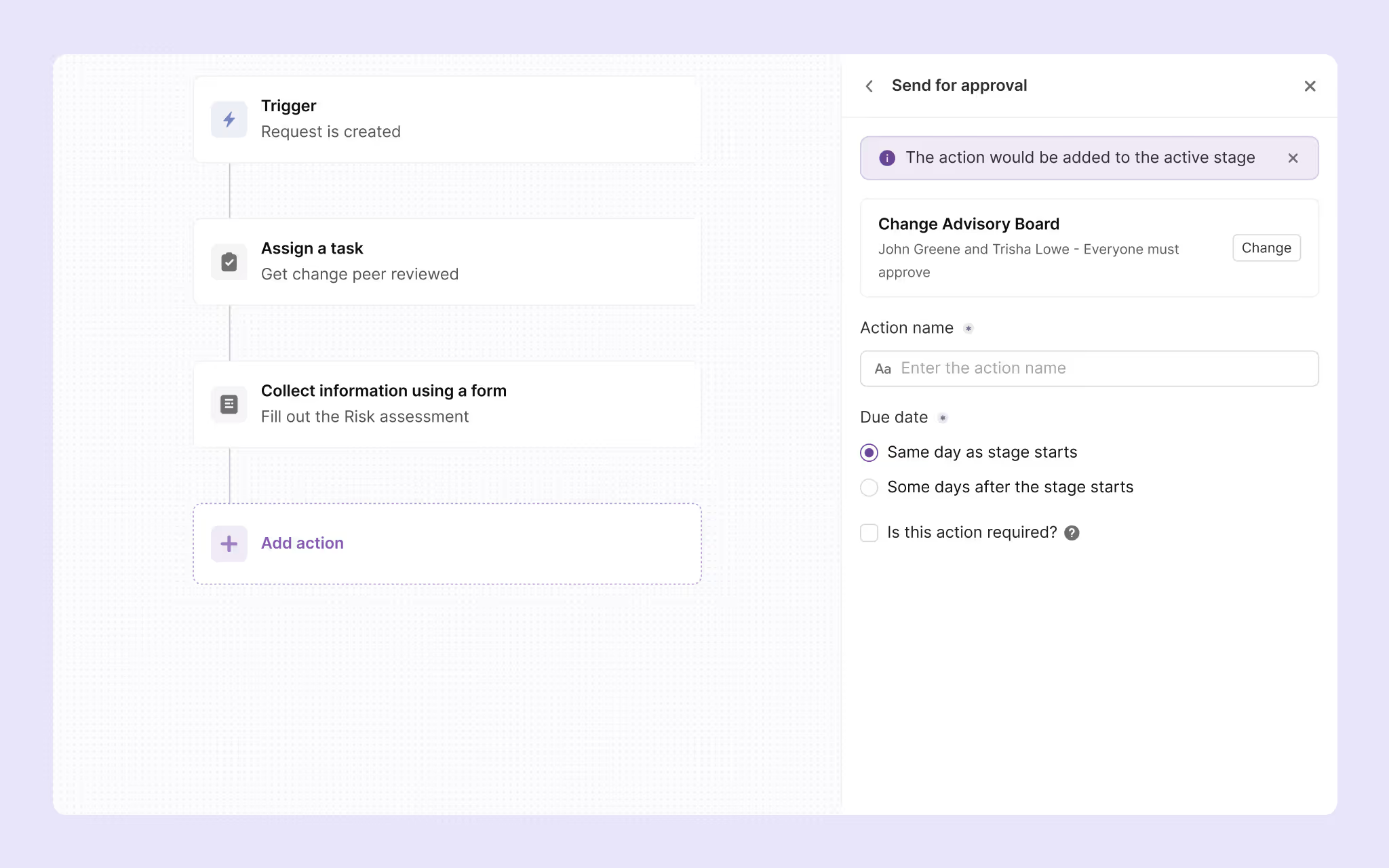
- Configure workflows to automatically enforce segregation of duties. The same person who requests a change shouldn't be able to approve and implement it. Your workflow system should prevent these conflicts and flag attempts to bypass controls. Modern ITSM platforms now offer configurable controls to prevent requesters from approving their own changes. This workspace-level setting eliminates conflicts of interest by automatically blocking requesters from approval workflows, excluding them from approver selection, and displaying clear error messages when they attempt to override these controls.
c. Maintain immutable audit logs
- Store all governance activities in tamper-evident formats that auditors can trust. This includes approval decisions, CAB meeting minutes, access grants, and any overrides or exceptions. Logs should capture not just what happened, but who made decisions and why.
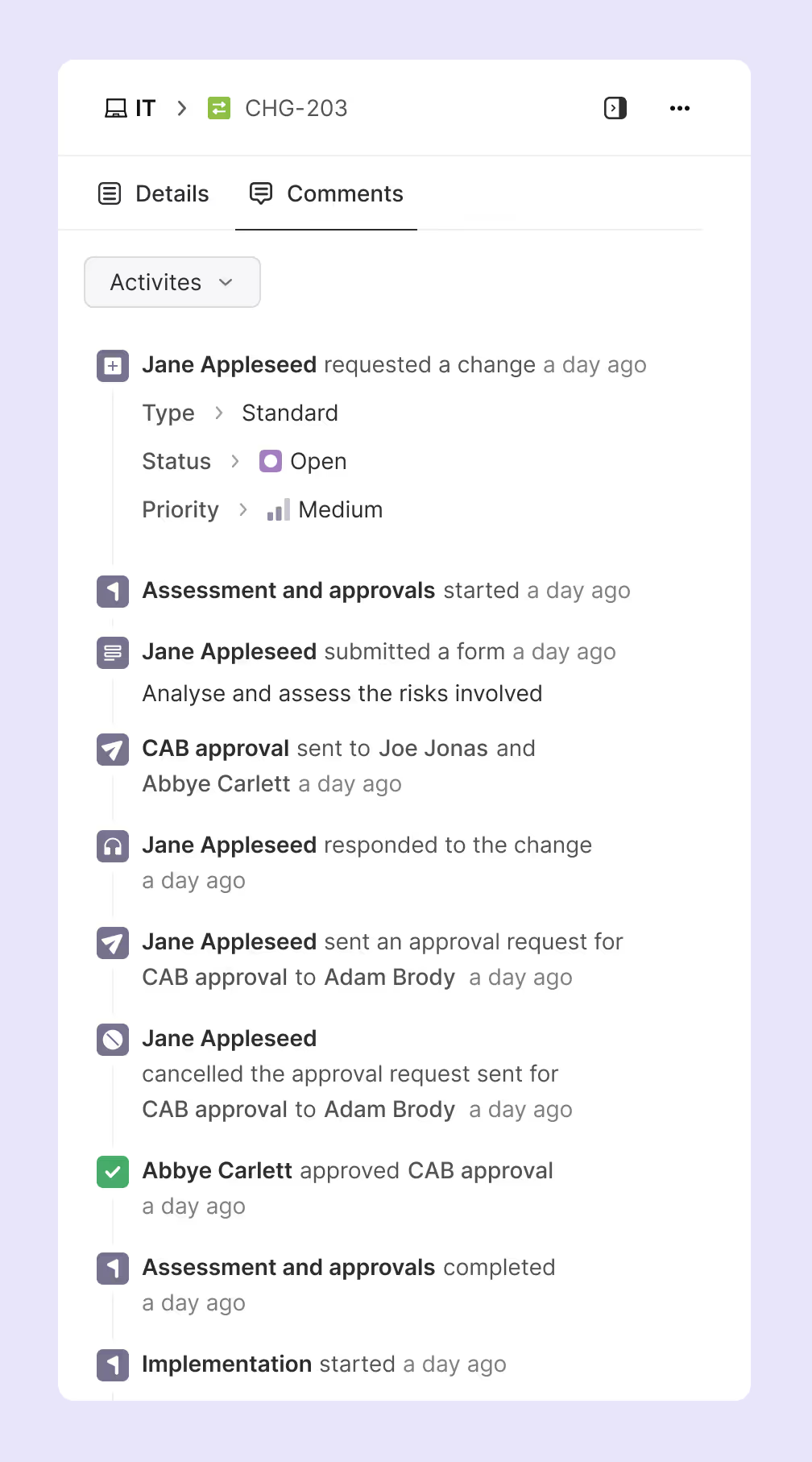
- Make sure to track the planned start date, planned end date, actual start date and actual end date for auditing purposes. Running an automated change management process via your ITSM platform will help automatically capture these details.
- Implement long-term retention policies that meet regulatory requirements, typically 3-7 years, as outlined in most frameworks. Ensure these logs remain searchable and exportable throughout the retention period. Auditors often need to trace specific changes or patterns across multiple years.
- Ensure external approvers have visibility into the change details they're asked to approve. End users assigned as change approvers should be able to view complete change information, including tasks and forms, directly within collaboration tools such as Slack or Teams.
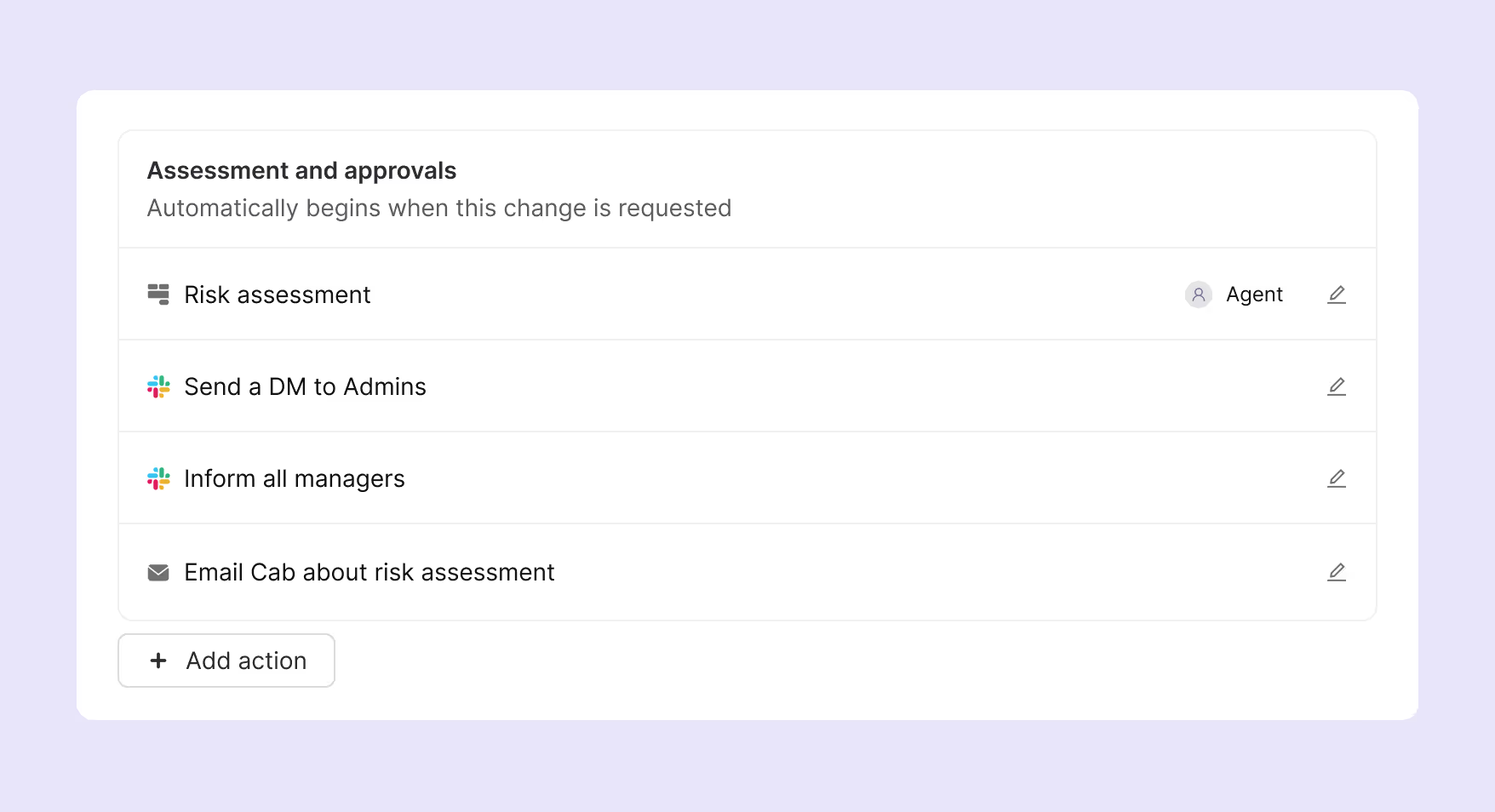
3. Technical impact analysis and dependency mapping
The last thing you want happening is to approve a straightforward database schema change until it breaks three applications nobody knew were connected. Without technical visibility into system dependencies, every change becomes an operational hassle.
a. Integrate change processes with configuration management databases
- Your CMDB should automatically map relationships between applications, databases, servers, assets, and network components. When someone proposes changing a database server, the system should immediately show all applications that connect to it, all dependent services, and any scheduled maintenance that might conflict.
- Use these mappings to simulate and automate impact analysis. If changing a load balancer configuration affects twelve applications across four business units, everyone involved should know before work begins, not after systems start failing. With dependency mapping, the system can scan for relationships between services, databases, and applications as soon as a change is logged to suggest an impact score.
- Modern ITSM platforms, powered by agentic AI, can bring this type of up-to-date, dynamic context on asset and potential impact dependencies for effective change management right within the admin's portal. When planning changes to core infrastructure, this deep context can help identify all systems that could be affected and all stakeholders who need notification.
b. Scope affected configuration items completely
- Every change request should identify all configuration items that will be modified, tested, or potentially impacted. This includes primary targets, dependent systems, monitoring tools, backup systems, and any integration points.
- Document and store current baselines for all affected items before implementing changes to maintain change history. This provides clear rollback targets and helps identify unauthorized modifications that might have occurred between planning and implementation.
4. Operational execution and change control
Your change plan looked perfect on paper, but nobody accounted for the maintenance window that conflicts with month-end processing, or the fact that the test environment doesn't mirror production configuration.
Poor execution planning turns approved changes into crisis management exercises when implementation details are vague.
a. Mandate comprehensive implementation plans
- Every normal and emergency change needs detailed implementation timelines with specific start times, duration estimates, and milestone checkpoints. Include resource requirements, technical dependencies, and coordination points where multiple teams need to synchronize activities.
- Document testing approaches that validate both functionality and performance in environments that mirror production. Testing should cover not just the changed component, but integration points and dependent systems that could be affected by the modification.
- Build rollback decision points into implementation timelines. Define specific criteria for when to abort implementation and invoke rollback procedures. This prevents teams from pushing forward with failing changes because they've already invested time and effort.
b. Conduct user acceptance testing
- Business stakeholders must validate that changes meet requirements and don't negatively impact business processes. UAT shouldn't be perfunctory checkbox testing, but genuine validation that changes solve intended problems without creating new ones.
- Structure UAT with specific test scenarios, acceptance criteria, and sign-off requirements. Document who performed testing, what scenarios were covered, and any issues or limitations identified during testing.
c. Use change calendars for sound coordination
- Maintain centralized calendars that give you one global view of all planned changes, maintenance windows, business events, and potential conflicts in one place. This prevents simultaneous changes that could compound problems and ensures changes happen during appropriate business windows.
- Define standard change windows during low-usage periods to minimize business disruption. Clearly communicate these windows to business stakeholders and enforce them consistently.
- Schedule regular calendar reviews where teams can identify potential conflicts and adjust their schedules accordingly. This coordination prevents the surprise discoveries that turn routine changes into emergency situations.

5. Rollback and recovery readiness
Your change failed at 2 AM, production is down, and your rollback plan consists of "reverse the steps we just took." Under pressure, with systems failing and stakeholders demanding updates, improvised recovery rarely works.
Without tested rollback procedures and clear recovery targets, failed changes turn into prolonged outages that disrupt business operations.
a. Document detailed rollback procedures
- Every change must include step-by-step rollback procedures with specific commands, scripts, and validation steps. These procedures should be complete enough that someone other than the original implementer can execute them successfully. Make it a best practice to include forms for roll-back and roll-out plans with every change to plan ahead.
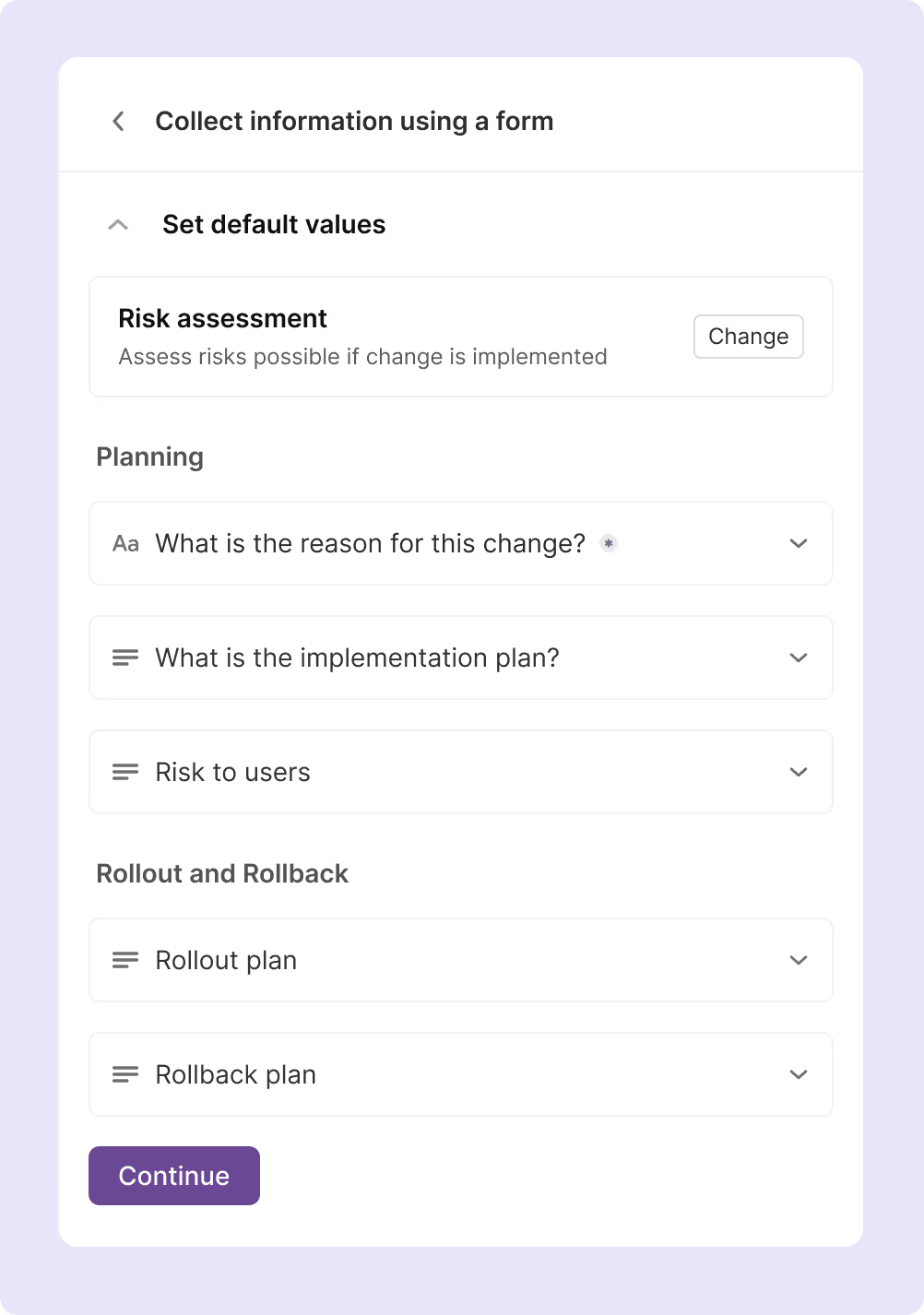
- Define recovery time objectives for each change based on business impact and system criticality. Document the maximum acceptable downtime and ensure rollback procedures can meet these targets. If rollback takes longer than acceptable downtime, the change needs additional planning or different implementation approaches.
- Store rollback documentation in centralized, easily accessible systems that remain available even when primary systems fail. Don't store rollback procedures on systems that might be affected by the change itself.
b. Test rollback procedures in staging
Rollback plans that haven't been tested are just wishful thinking.
- Use staging environments that mirror production to validate that rollback procedures work and meet recovery time objectives.
- Document rollback testing results and any modifications needed to make procedures work reliably. Include timing estimates, resource requirements, and any manual steps that can't be automated.
- Schedule regular rollback testing for critical systems, not just when changes are planned. This validates that rollback procedures remain viable as systems evolve, helping teams maintain proficiency with recovery processes.
c. Prepare for data recovery scenarios
- Changes that affect data require special consideration for rollback and recovery. Document data backup procedures, restoration points, and validation steps to ensure data integrity after rollback operations.
- Consider scenarios where partial rollback might be necessary, such as when some components of a change succeed while others fail. Plan for situations where rolling back creates data consistency issues that need resolution.
- Test data recovery procedures with realistic data volumes and complexity, not just sample datasets. Production data recovery often reveals performance and complexity issues that don't appear in simplified test scenarios.
Building compliance that works for effective change management
When you embed governance into your change workflows, classify changes by actual risk, and build rollback procedures that teams can execute under pressure, compliance becomes less of an administrative burden.
Modern platforms, such as Atomicwork, are making this transition easier by embedding compliance controls directly into change workflows, thereby eliminating the gap between doing the right thing and proving that you did it.
If you’re interested to see how our change management workflows can help your business, reach out to us.
Frequently asked questions

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph

Faq answer paragraph
You may also like...

































