User Provisioning for Modern Enterprises [Challenges + Tips to Overcome]
Your organization is growing rapidly. Your hiring pace has picked up and so have the complexities within your onboarding and access provisioning processes. HR and IT teams are now under immense stress to create accounts, set up devices, and assign permissions for every new employee promptly.
This is generally a tedious process – giving access to different applications to different employees– especially in larger organizations. This is where user provisioning helps. Simply put, it's the process of ensuring the right people have the right access to the right resources, at the right time.
But why is effective user provisioning so important at modern enterprises? Let's understand its need, its benefits, and its effectiveness in improving efficiency and security within your organization.
What is user provisioning?
As per Gartner, 'User provisioning or account provisioning technology creates, modifies, disables and deletes user accounts and their profiles across IT infrastructure and business applications.'
Imagine a well-oiled machine – when a new employee joins, their account is automatically created in all the necessary systems with the appropriate permissions, allowing them to hit the ground running. If an engineer joins, they get access to Postman and Jira. If a designer joins, she automatically gets access to Figma and Adobe. If a copywriter joins, she directly gets access to Notion and WordPress. If an accountant joins, she directly gets access to Zoho and so on.
Why user provisioning matters?
According to a report published by Gartner in 2023, a desk worker uses an average of 11 apps to complete their tasks. Among these, as many as 40% digital workers use more than 11 applications while 5% use more than 26 apps for work.
Imagine a company with hundreds or even thousands of employees like these. Each employee might need access to a variety of applications, such as email, project management tools, customer relationship management (CRM) software, and more. Manually creating and managing these accounts can be a time-consuming process and more often than not, delay the onboarding by a couple of days.
User Provisioning makes this process faster and easier for both employees and the IT team. Here is how:
For employees
- Expedite onboarding: New employees don't have to wait for IT to manually create accounts in all the different systems they need. With user provisioning, they can get direct access to software or applications they need.
- Enhance experience: With instant access to the tools they need, new hires can start working right away. This reduces frustration and helps them feel more comfortable and engaged in their new role.
For employers
- Improved security: Manual account creation can lead to human error, potentially granting unauthorized access or forgetting to remove access for departing employees. Automated provisioning ensures consistent and accurate access control.
- Enhanced efficiency: Automating repetitive tasks like account creation and permission assignment frees up IT staff to focus on more strategic initiatives.
- Compliance: User provisioning helps organizations comply with data privacy regulations by ensuring appropriate access control and audit trails.
Benefits of user provisioning
By implementing a user provisioning system, organizations can reap several benefits:

- Simplified onboarding: New hires gain immediate access to the systems and applications they need to be productive, reducing onboarding delays.
- Streamlined offboarding: When an employee leaves, their access is automatically revoked, preventing potential security risks and data breaches.
- Improved user lifecycle management: User provisioning facilitates lifecycle management by automating account creation, updates in case of promotion or department change, and eventually, deactivation of accounts and access upon departure.
- Enhanced security posture: Automated provisioning reduces human error and enforces consistent access controls, minimizing unauthorized access risks.
- Increased IT efficiency: Saving time spent on manual account management tasks, IT staff can focus on more strategic initiatives like security maintenance and user support.
User provisioning process: a step-by-step look
A typical user provisioning process involves a series of steps as explained below:
- Define your needs: First, consider the size of your company and the complexity of your IT environment. What kind of user access do you need to manage? This will help determine the features and level of automation required in your system.
- Choose the right tools: There are various user provisioning solutions available, ranging from simple software to comprehensive identity and access management (IAM) platforms. IT Teams can consider the organization’s budget and needs when selecting the best tool for their company.
- Design your user access workflow: Map out the process for user provisioning, including how user requests are triggered (new hires, promotions, etc.), what information is needed, and how access levels are determined.
- Integrate with existing systems: A great user provisioning system should connect with the HR system, directory services, and other relevant applications to ensure smooth data flow and account creation.
- Implement and test: Once your system is set up, thoroughly test it to ensure it functions as expected. This includes testing different user scenarios and access levels.
- Establish governance: Define clear policies and procedures for user provisioning, including who can request access, what approvals are needed, and how access is reviewed and revoked.
A good user provisioning system is invisible.
Imagine a new marketing employee, Sarah, joining the company. The HR department initiates a user provisioning request. The identity management system, based on Sarah's department and role, automatically creates accounts for her in the CRM system, marketing automation platform, and company email system. Sarah receives login credentials and can access the tools she needs to start working on marketing campaigns right away. When Sarah is promoted to a senior marketing role, her access permissions are automatically adjusted to reflect her new responsibilities.
User provisioning elements
User provisioning involves several key elements working together to ensure users have the right access to company resources. Here's a breakdown of the main ones:
- Identity repository acts as a central hub that stores all user information, such as names, departments, job titles, and other relevant details.
- Provisioning engine is the core of the system, automating the process of creating, modifying, and deleting user accounts across various applications and systems. Think of it as the machine that reads your information from the identity repository and creates user accounts for the right applications.
- Role management defines different user roles within the company (e.g., manager, salesperson, customer service representative) and assigns specific access permissions to each role.
- Workflow management establishes the process for requesting and approving user access. It outlines who can request access, what information is needed, and any necessary approvals.
- Policy management defines the rules and regulations for user provisioning, such as how long access lasts for temporary employees or what happens to accounts when someone leaves the company (deprovisioning).
- Access request and approval allows authorized personnel (like managers) to submit requests for user access and grant or deny approvals based on established workflows and policies.
- Integration and synchronization ensure your user provisioning system connects seamlessly with other relevant systems, such as HR platforms and directory services. This allows for smooth data flow and account creation.
- Security and authentication ensure that only authorized users can access the system and manage user accounts. Multi-factor authentication (MFA) is often used for an extra layer of security. Imagine having a secure lock on the key system itself (user provisioning) and maybe even needing a fingerprint scan (MFA) to access it.
User provisioning best practices
Here are some best practices to consider when establishing a user provisioning system:
- Prioritize automation: Automate as much of the user provisioning process as possible, including account creation, permission assignment, and access revocation. This saves time, reduces errors, and improves efficiency.
- Centralized identity management: Implement a central system, like an Identity and Access Management (IAM) platform, to manage all user identities and access across all applications and systems. This creates a single source of truth and simplifies user provisioning.
- Enforce multi-factor authentication (MFA): Add an extra layer of security by requiring multiple factors for user login, such as a password and a verification code.
- Monitor and audit user activity: Track user activity in your systems to detect any suspicious behavior. This can help identify potential security breaches.
- Stay compliant: Ensure your user provisioning system adheres to relevant industry regulations and data privacy laws.
- Least privilege principle: Follow the principle of least privilege, granting users only the minimum access level required to perform their jobs. This minimizes the risk of unauthorized access and data breaches.
- Role-based access control (RBAC): Define user roles with specific access permissions. This makes user provisioning easier and ensures users only have access to the resources they need.
- User education: Educate users about cybersecurity best practices and the importance of responsible access management. This can help prevent accidental data leaks or misuse of access privileges.
- Scalability: Choose a user provisioning system that can scale with your organization's growth. This ensures the system can accommodate future increases in users and applications.
- Regular reviews and audits: Regularly review user access and conduct audits to ensure continued compliance with security policies and regulations. This helps identify and address any potential security risks.
Challenges in manual user provisioning
On the surface, manual user provisioning might seem like a straightforward task, but it comes with its own set of challenges like delays and security breaches. Here is a list of common challenges faced while using manual user provisioning:
- Time-consuming: Manually creating and managing user accounts across multiple systems can be a tedious and slow process, especially for large organizations. Imagine an IT team swamped with individual requests for access to dozens of applications – it bottlenecks the onboarding process and delays new hires from becoming productive.
- Prone to errors: Manual data entry is susceptible to mistakes. A typo in a username or granting the wrong access level can lead to security vulnerabilities or hinder a user's ability to do their day-to-day job.
- Inconsistency: Without a centralized system, user provisioning practices may vary across different departments. This inconsistency creates security gaps and makes it difficult to manage access controls effectively.
- Compliance risks: Many regulations require companies to track user access and activity. Manual processes make it difficult to maintain accurate records and audit trails, potentially leading to non-compliance fines.
- Security concerns: Manual provisioning often leads to delays in deprovisioning user accounts, especially for departing employees. This can leave your data vulnerable to unauthorized access if old accounts remain active.
Don’t keep your employees waiting!
Monetarily speaking, it is not a good idea to delay the onboarding process of your new hires. Invest in user provisioning to save time and enhance employee experience.
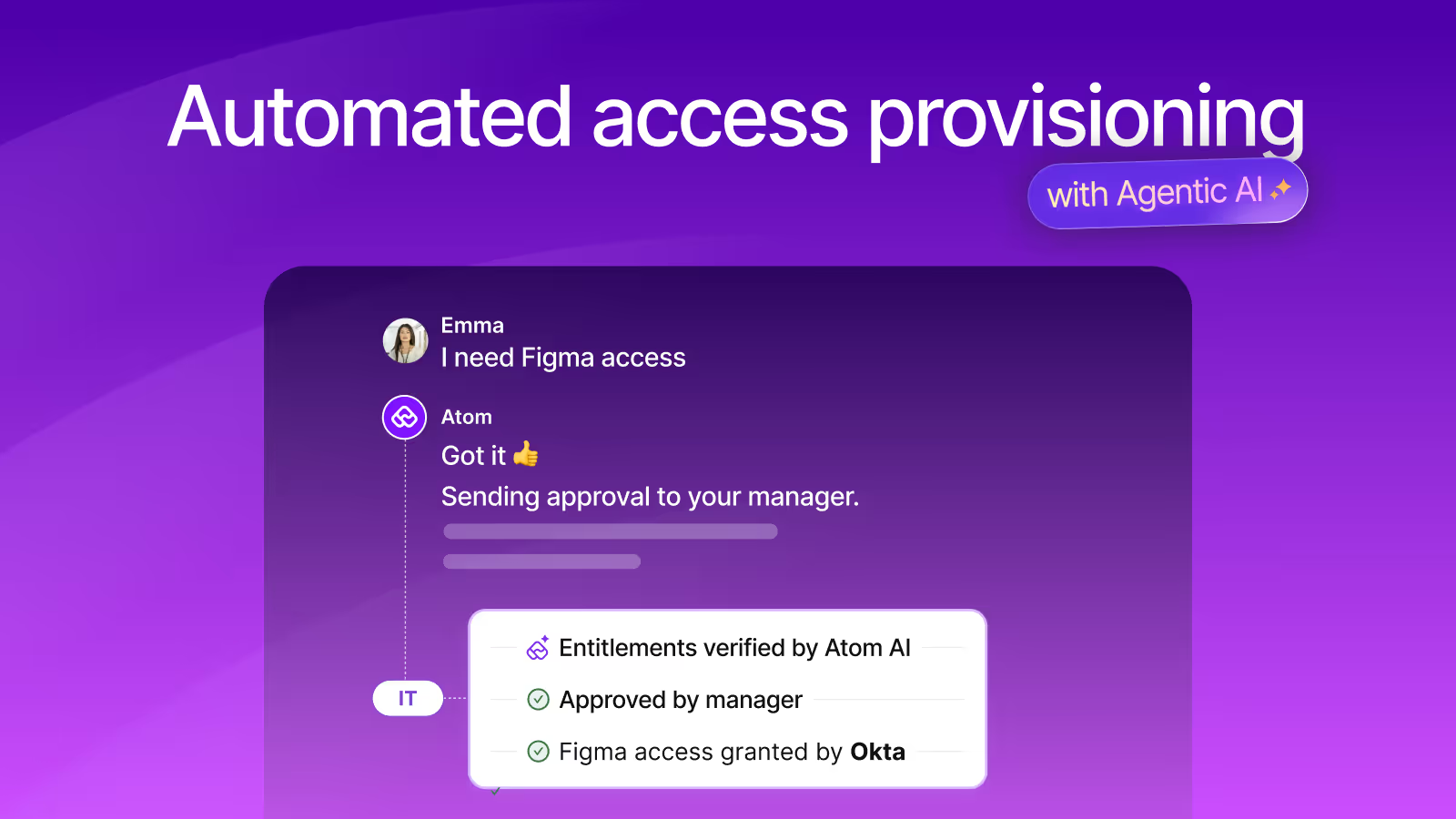
Atomicwork integrates with top access management tools like Azure directory and Okta to automate user provisioning. Once the IT Team sets workflows, Atomicwork ensures the onboarding and offboarding processes run smoothly. This ensures new employees get all the access and app permissions they need quickly and efficiently.
Similarly, when an employee leaves the company, offboarding workflows help follow security best practices to minimize the risk of unauthorized access. This reduces the chance of human error and makes the entire process smoother for everyone involved.
Got more questions on how you can automate your user provisioning? Contact us and we're happy to assist!
Frequently asked questions
Automated user provisioning is the process of automatically managing the creation, updating, and deletion of user accounts and access rights within an organization’s IT systems. This automation maybe managed via an identity and access management (IAM) system, streamlining the onboarding and offboarding processes and ensuring that users have the appropriate access to resources based on their roles.
User provisioning ensures accuracy in assigning access rights, minimizing errors and ensuring users have appropriate permissions. It also reduces unauthorized access risks by promptly updating access rights and deactivating accounts. It supports compliance by maintaining accurate records and audit trails of user access. Additionally, user provisioning ensures consistent application of access policies across all systems, streamlining IT operations and improving overall organizational security and efficiency.
User Authentication is the process of verifying the identity of a user attempting to access a system. It ensures that the user is who they claim to be through methods like passwords, biometrics, or multi-factor authentication (MFA). User provisioning, on the other hand, involves the creation, management, and maintenance of user accounts and access rights of employees within an organization.
Yes, of course! Atomicwork can allow you to automate user provisioning for your employees from the time you onboard them, through their job role changes, up to their off boarding. You can manage employee access and their permissions via Azure directory or Okta easily with Atomicwork.
More resources on modern ITSM
.avif)